A website ending in .pr.gov belongs to an official organization of the Government of Puerto Rico.
Secure websites use HTTPS, which means that you are connected securely to this pr.gov website.
What are CISA's Cyber Hygiene Services?
This free subscription allows Licensees to carry out a self-assessment of their IT assets and receive mitigation recommendations from CISA. The recurring scans include:
What are the objectives of CISA's Cyber Hygiene Services ?
Who performs these scans and who can receive the information?
Cyber Hygiene services are provided by CISA’s highly trained information security experts equipped with top-of-the-line tools. CISA's mission is to measurably reduce cybersecurity risks to the nation by providing services to government and critical infrastructure stakeholders.
U.S.-based federal, state, local, tribal and territorial governments, as well as public and private sector critical infrastructure organizations are welcome to enroll, free of charge. The report is sent only to the contact registered for your organization, once the Service Request Form (SRF) and the legal documentation required by CISA has been submitted.
Will CISA send the vulnerability scans directly to the Office of the Insurance Commissioner (OCS)?
No. This service is available for Licensees who choose CISA as a provider of vulnerability assessments and mitigation recommendations, free of charge.
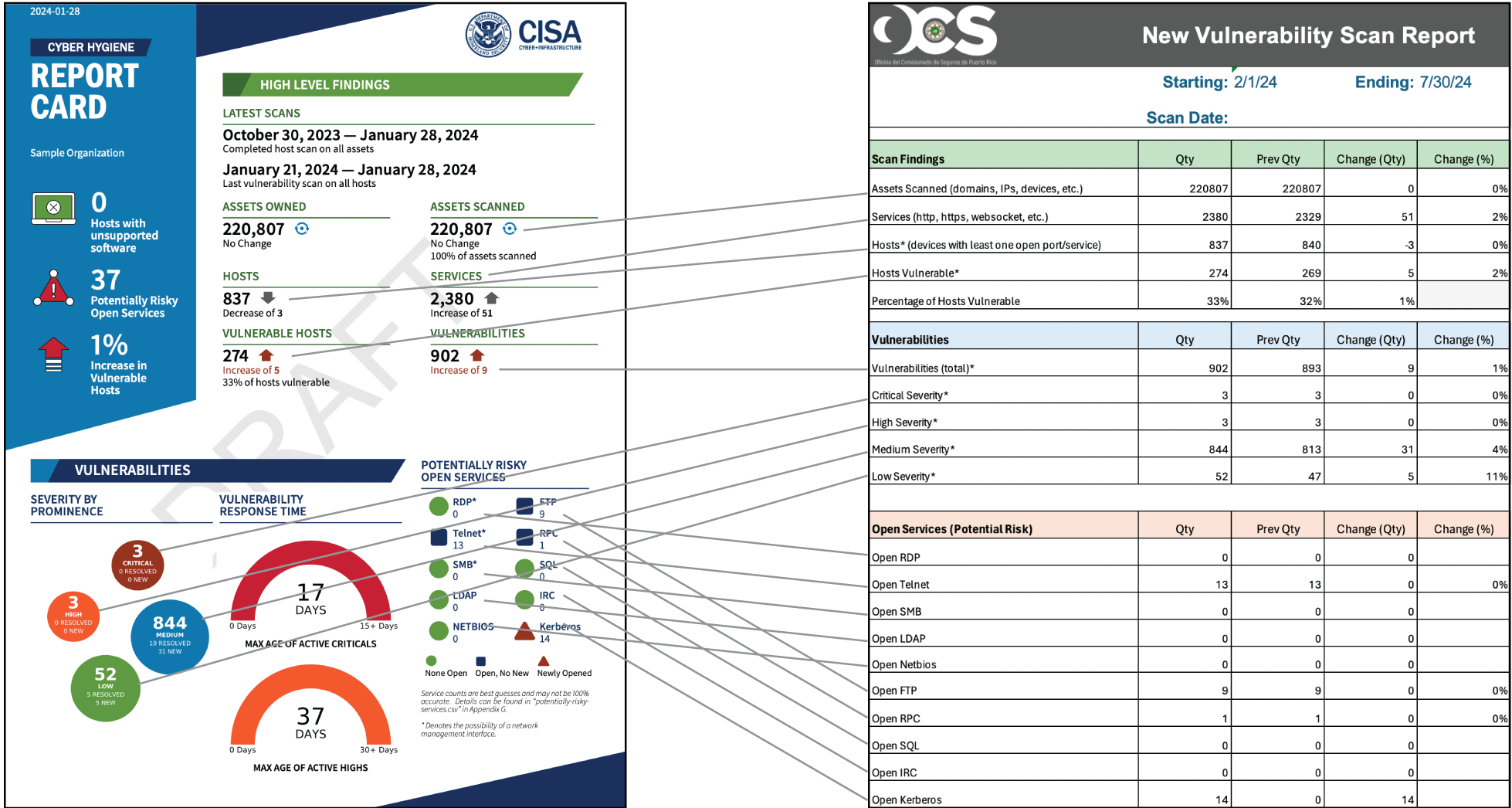
Each Licensee shall report to the OCS the results of its vulnerability scans twice a year, regardless of the service provider they choose. Licensees who are enrolled in CISA's Cyber Hygiene Services can easily find the information required to prepare their reports on page 6, titled Cyber Hygiene Report Card.
How often are scans performed?
Once you have been enrolled in the Cyber Hygiene Services, CISA will send you your first scan by email the Monday after the first analysis.
The analysis is carried out continuously between each weekly report. Any device that is detected with at least one open port or service is considered a host. The prioritization schedule of the Cyber Hygiene Services is as follows:
· Addresses without active services detected (dark space) are re-analyzed after at least 90 days.
· Hosts without detected vulnerabilities are re-analyzed every 7 days.
· Hosts with low-risk vulnerabilities are re-analysed every 6 days.
· Hosts with medium-risk vulnerabilities are re-analyzed every 4 days.
· Hosts with high-risk vulnerabilities are re-analyzed every 24 hours.
· Hosts with critical risk vulnerabilities are re-analyzed every 12 hours.
It is important to consider that a single host can have multiple vulnerabilities of different severity, which affects the frequency with which a host is scanned.